Wireless LAN Operation
Basic Service Set (BSS)
802.11 describes the concept of the Independent Basic Service Set (BSS) which is in effect a Wireless LAN subset, or cell,
consisting of the clients and perhaps a Base Station called
an Access Point (AP). The most basic BSS is that between just two clients. This is called
an Ad-Hoc Network where clients have wireless adapters and can talk to each other i.e. Peer-to-peer, but there is no connection
point to a Distribution System (DS) via an Access Point.
Basic AP functions such as beaconing and synchronisation can be carried out by the client in Ad-Hoc mode, however functions such
as power save and relaying frames cannot be done. A Distribution System is the backbone network connection
which can be a wired or a Wireless LAN. A number of BSSs along with the associated DS form the Extended Service Set (ESS).
A Portal is a function that provides 'bridging' between a 802.11 LAN and another 802 LAN. This function is typically
performed by the AP.
An individual station becomes associated with a particular BSS. This association is dynamic because a station is not fixed to one place
as it would be in a wired environment. An Access Point is a particular type of station that provides access to the DS, which is normally
a wired LAN.
Inter Frame Spaces (IFS)
802.11 defines five inter frame spaces:
- Short Inter Frame Space (SIFS) - separates transmissions within a session between two stations.
This is different depending on the Physical layer technology is being used e.g. the value is 28us for FHSS.
The SIFS is important because it ensures that ACKs are always sent with the highest priority and prevents
a station transmitting before an ACK is sent.
- Point Coordination IFS (PIFS) - is the time used by the AP during PCF to gain access to the radio band before
other stations. This is the SIFS plus one slot time and amounts to 78us.
- Distributed IFS (DIFS) - is the normal silence time between frames used when a station wishes to begin a fresh transmission.
It is caclulated as the SIFS plus two slot times and is 128us.
- Extended IFS (EIFS) - this is used when a station cannot understand the duration time in a received packet,
it therefore prevents a collision with a packet within the same data stream and is sent at the slowest supported rate in the cell.
In 802.11g/a the EIFS is 364us and is made up of SIFS plus 8 x ACK + preamble length + PLCP Header length + DIFS
- Reduced IFS (RIFS) - used with 802.11n frame bursts and is 2us.
The time lengths vary depending on the wireless protocol. The following table gives common values:
| Protocol |
SIFS (us) |
Slot Time (us) |
PIFS (us) |
DIFS(us) |
| 11b |
10 |
20 |
30 |
50 |
| 11g |
10 |
9 |
19 |
28 |
| 11a |
16 |
9 |
25 |
34 |
Station Transmission and CSMA/CA
The MAC layer in 802.11 is similar to the MAC layer in other LAN technologies however in wireless it has additional tasks
such as packet retransmission, fragmentation and acknowledgments. The Physical layer covers the
technologies DSSS, FHSS, Infra Red etc. used to carry the data over the radio.
Wireless devices operate at half-duplex and there are two provisions for accessing the wireless LAN;
the Point Coordination Function (PCF) and the Distributed Coordination Function (DCF).
The rarely used Point Coordination Function uses a smaller interval designated PIFS in order that the AP
may give time-sensitive traffic such as VoIP or Video greater priority i.e. the AP is a central point of coordination.
APs send Beacon frames at regular intervals (commonly 0.1 second). Inbetween these beacon frames,
there are defined two time periods: the Contention Free Period (CFP) and the Contention Period (CP).
During the CP, the DCF is used. With CFP, the AP sends Contention Free-Poll (CF-Poll) packets to each station in
turn that has urgent traffic to send,
in order to enable them to be able to send a packet. Although CFP gives some QoS, there is no granularity.
Most commonly used is the Distributed Coordination Function uses Carrier Sense Multiple
Access with Collision Avoidance (CSMA/CA) where no device centralises the control of who is going to send next.
The difference of a wireless medium c.f. wired medium is that
we cannot guarantee that every station will detect if another is sending data (unlike the wired environment
where there is an obvious voltage change). For instance, a station 'A' that is detected by an AP may be too far
from another station 'B' that is also detected by that AP. This is known as the Hidden Node Problem.
For this reason the use of Clear to Send (CTS) has been introduced into the collision detection algorithm.
The steps taken in order for a station to transmit are as follows:
- A station wishing to transmit a frame first sends a small control packet called Request to Send (RTS).
This contains the source, the destination and the duration of the transaction i.e. how long it would take to transmit the frame. This duration time
includes the time for the ACK to be sent and received.
- The receiving station responds with a control packet called Clear to Send (CTS) with the same
duration information.
- Any station that sees either the RTS or CTS sets its Network Allocation Vector (NAV) for the specified
duration within the control packets. This is called Virtual Carrier Sense and the NAV State is used as well as
physically detecting the radio waves for other talkers before transmitting. Because Virtual Carrier Sense
uses small frames this means that less bandwidth is used in a collision than if normal long data frames collide.
- The station now physically senses the radio waves to see if another station is transmitting, this is called
Clear Channel Assessment (CCA).
- It waits for a period of time called the Distributed Inter-Frame Space (DIFS) and then transmits
- The receiving station (given by the destination MAC address) checks the CRC of the frame and sends
back an ACK. This is where the 802.11 MAC differs from other MACs.
- If the originating station receives the ACK then it can assume that no collision occurred. If no ACK
is received then the transmitting station tries again
- If there is a collision or a failure in transmission then the Binary Exponential Backoff Algorithm is invoked whereby the
station picks a new random number that is twice that of the previous one thereby creating a period of time called
the Extended Interframe Space (EIFS). This process is repeated on the event of further collisions, the random number
can go up to 1023.
The Binary Exponential Backoff Algorithm
When a collision occurs, each station chooses a number of slot times between '0' and a number 'n'
from which the station picks a random number. The number 'n' is typically 31 for 802.11b and 15 for
802.11a/g/n. The station then adds its NAV value to the countdown timer and counts down from the resulting total.
Each station then waits the allotted time by counting down whilst still listening to the media before trying to communicate again.
If the station detects a conversation then it pauses the countdown until the conversation has finished
at which point it resumes the countdown. The total amount of time that the station waited (countdown time plus
paused time) is called the Contention Window (CW). If a further collision occurs then the
number 'n' is increased exponentially so that a much greater range of number of slot times are available
for this busy network of talkative stations.
This Binary Exponential Backoff Algorithm is invoked on detection of a collision, after a retransmission has occurred
and after a successful transmission too.
Two parameters define the Contention Window:
- aCWmin - minimum CW size (31 for 802.11b and 15 for 802.11a/g/n), the random backoff algorithm initially uses this
- aCWmax - maximum CW size (1023), the retry counter has the increment 'n' added to aCWmin, on subsequent collisions 'n'
is doubled and again added to aCWmin until it reached aCWmax.
Fragmentation and Reassembly
In this radio LAN environment there is more chance of larger frames being corrupted than smaller ones. This
is mainly due to radio being less reliable than wired environments, but also due to there being more chance
of collisions and interruptions because of frequency hopping that stops the radio for short periods e.g. 20ms.
To counter this, 802.11 allows for fragmentation and reassembly of frames. A data frame is called
a MAC Service Data Unit (MSDU) which can be as large as 2346 octets, however it may be fragmented
into smaller MAC Protocol Data Units (MPDU). Each MPDU has a copy of the MAC header and a CRC at the end.
The sending station has to receive an ACK for each MPDU before it sends the next ACK.
Losing a smaller MPDU through collision or some other
interruption causes less disruption that losing the whole MPDU.
Joining a BSS
A station joins a BSS using one of two methods:
- Passive Scanning - where the station just waits for a periodic Beacon Frame from the AP.
This frame provides synchronisation information amongst other things.
- Active Scanning - where the station sends a Probe Request Frame to discover an AP.
The AP responds with a Probe Response Frame
.
Synchronisation is important because frequency hopping has to occur seamlessly with no errors in transmissions.
The AP sends periodic Beacon frames that contain the value of the AP's clock at the time of transmission.
The stations use this clock value to synchronise their own clocks.
Power Saving
By default wireless LANs operate in Constant Access Mode (CAM) which means that the Wireless transmitter is always
on listening for traffic.
Stations can however go into a sleep mode called Polled Access Mode (PAM) whereby the station sends a null frame with the sleep bit
set to 1. Then without losing frames, the APs buffer packets due for the station
until the station comes out of sleep mode. The AP sends out the information on which stations
have frames due to them within frames called Traffic Information Maps (TIM). These TIMs
carry station identifiers and are
received by the client because the client wakes at regular intervals just long enough to receive whatever frames have been buffered for it
before it goes back to sleep. If the client sees its own identifier in the TIM then it sends a Power-Save Poll (PS-Poll) to the AP
in order to ask the AP to forward on the buffered frames.
If broadcast traffic is available then the AP sends a Delivery Traffic Information Map (DTIM).
DTIM and TIM timers can be adjusted at the AP.
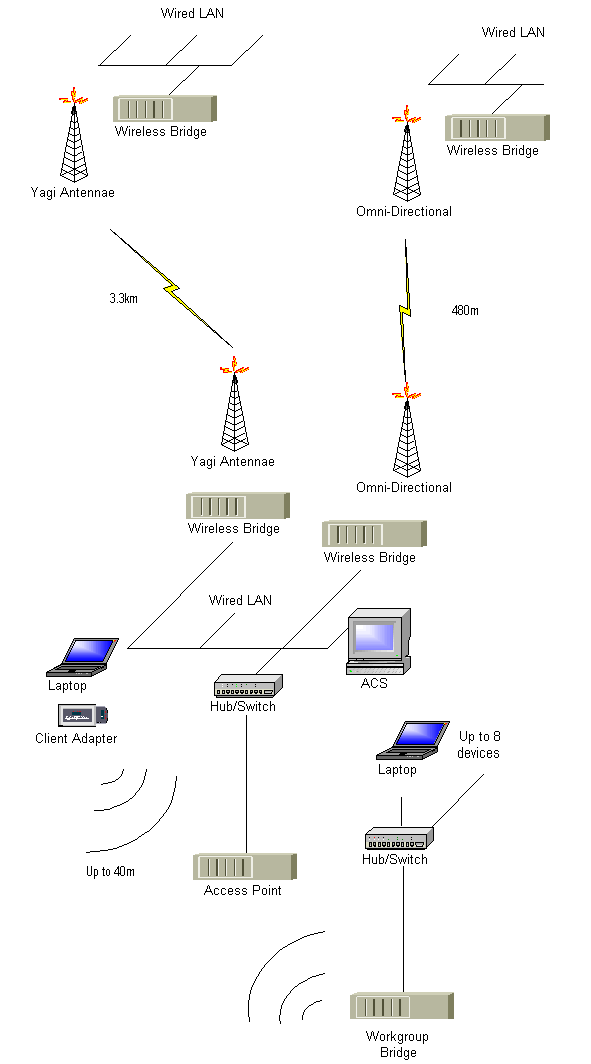
Physical Architecture
The components of a Wireless network consist of the following:
- Client Adapter - for client access to the wireless network in PCI or PCMCIA
format, typical indoor range @11Mbps is 40m when running at Transmit power of 100mW or 30m at 30mW.
- Access Point (AP) - Central point of shared access for wireless clients, analogous to the shared Ethernet hub in a
wired environment. The AP normally has a 10/100BaseT uplink port which can often use inline
power to power the AP. The Transmit power of the AP can be varied to reduce cell size.
Often, up to 3 APs can be located together to provide 33Mbps aggregate bandwidth, or load balancing based on user numbers, error rates
or signal strengths. You can also have a redundant hot standby AP to take over from the primary in case of failure.
At this point, filtering based on broadcasts/multicasts and IP/IPX sockets numbers can be set up to maximise the available bandwidth.
- Workgroup Bridge - this provides connectivity for a number of
wired Ethernet devices to a wireless LAN. You need a hub to connect these devices,
and then you connect the hub to the 10BaseT port on the Workgroup Bridge.
- Wireless Bridge - This is designed to provide long range external wireless connectivity, typically between buildings
and can provide Point-to-point or Point-to-multipoint connectivity. Operating power comes from the inline power within the Ethernet
connection. The Wireless Bridge comes with two RP-TNC connectors for antennae.
- Antennae - for transmitting and receiving specific frequencies e.g. 2.4GHz. The following antennae are typical:
- Client Antennae
- Access Point Antennae which can also be used to bridge between buildings up to 1km
- Bridge Antennae specifically for bridging between buildings within line of site, mainly with the use of masts. Distances exceeding
18km can be achieved.
- Low Loss Antennae Cable - In order to extend the distance between the antenna and the bridge use this cable which typically has a loss
of 6.7dB/30m.
- Access Control Server - an Access control server that can run RADIUS or TACACS+ for AAA can be used to enhance security within the
Wireless network
A typical Wireless Topology could look like the following:
Cisco's Aironet 350 system uses 2.4GHz and Direct Sequence Spread Spectrum (DSSS)
technology (where the radio frequency is spread continuously over the specified frequency band)
at 100mW transmit power. The modulation used at 1Mbps is
Differential Binary Phase Shift Keying (DBPSK), at
2Mbps - Differential Quadrature Phase Shift Keying (DQPSK) and at 5.5 and 11Mbps - Complementary Code Keying (CCK).
There can be up to 3 non-overlapping channels allowing 11 x = 33Mbps aggregate throughput if desired.
Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA) is used at the data link layer, note the difference
of 'Collision Avoidance' compared with wired Ethernet LAN technologies which use 'Collision Detection'. This difference exists
because there is no way of detecting a collision in the wireless environment.
Cisco also has a 340 series. The differences are that the Power Output is 30mW (c.f. 100mW with 350 series) and it uses a single
dipolar antenna by default
in the client adapters. The resultant maximum range indoors @11Mbps is 30m (c.f. 39.6m with 350 series).

|

