Wi-Fi Security
Introduction
The obvious difference between a wired network system and a wireless network system is that the wires physically
restrict access to the transmission medium whereas a wireless medium is available to anyone who may be in range
of the signal. For this reason it is important to secure the wireless medium sufficiently enough
to give confidence that wireless is secure and private enough to be used seriously. This is the challenge
of Wireless Fidelity security.
As with all network security, it is important to not only encrypt (hide) data but also to ensure that the data
has not been interfered with (integrity) and that the user has been authorised to receive the data.
Following is a description of the mechanisms that have been introduced to secure the WiFi network. Over time
these methods have increased in complexity and effectiveness.
In order to tackle the issue of security i.e. preventing unauthorised access to the data transmitted via the radio waves, a number of
technologies have emerged and these are detailed in order of complexity.
Service Set Identifier (SSID)
The first of these technologies is called the Service Set Identifier (SSID). The SSID is a basic naming handle
and is a network name consisting of 32 ASCII characters for a set of devices in a Wireless subsystem.
The SSID logically segments the Wireless LAN and
the SSID must be shared by the client and the access point. The SSID must not contain spaces or unusual characters.
By default the SSID is broadcast by the access point but it can be set not to.
The problem with the SSID is that it is not really secure even if it is not broadcast by the AP. This is because
the client is able to see the SSID within the header of the beacon frame issued by the AP. In addition,
if the client has no SSID configured i.e. a null string, then it will associate with an AP no matter
what SSIDs the AP is using.
Another issue with the SSID method is that authentication is not mutual i.e. the client does not authenticate
the AP so a rogue AP could broadcast the same SSID and the client attach to the rogue instead.
It is possible for an AP to filter clients based on the MAC address of the clients Wi-Fi adapater. This then
restricts which clients are allowed to associate with the AP. This however, only provides a basic level
of security since a determined hacker can analyse the Wi-Fi traffic and spoof an acceptable MAC address
to gain access. In addition, MAC address filtering still does not provide mutual authentication.
Wired Equivalent Privacy (WEP)
The next of these technologies is the Wired Equivalent Privacy (WEP) which was built in to the 802.11 standard.
WEP is optional and is designed to give a level of link integrity equal to that of a cable. Encryption used for WEP can be
either 40-bit or 104-bit encryption. The key is used within a stream cypher called Rivest Cipher 4 (RC4).
An RSA-based chipset is used to perform the encryption and decryption.
The algorithm is considered to be symmetric in that the same key and algorithm are used for both encryption and decryption.
In order for the Wireless Ethernet Compatibility Alliance
(WECA) to give Wi-Fi certification to a system, at least a 40-bit encryption level for WEP had to be used,
and this was defined within 802.11. WECA has now become the Wi-Fi Alliance.
With RC4 an Initialisation Vector (IV) is added to the beginning of each key. This vector is 24 bits long, consequently you
will often see the WEP keys lengths referred to as 64-bit and 128-bit.
The Initialisation Vector is a block of bits that is necessary to allow a stream or block cypher to be run in
different streaming modes of operation to produce a unique stream that is independent from other streams produced by the same
encryption key. This is without having to go through a process of re-keying.
Defining the keys can happen in one of two ways:
- The use of up to four default keys. These default keys are learned by all devices in the subsystem and they use these
keys to talk securely with each other. The issue here is that the more devices there are, the more widely-known become
the default keys and therefore the network becomes less secure.
- The use of unicast key mapping so that a key is only shared between any two stations. This is more secure but is more
problematic in the distribution of these unicast keys.
Authentication of the client can happen in either of two ways, an Open key method, or a Shared key method.
Whichever method is used must be the same for the whole subsystem i.e. the devices and the AP.
Open Authentication
This is the default mechanism and allows the whole authentication process to occur openly
in clear text so that any client can associate with the AP, even if no key has been set up or if the
client supplies an incorrect key. The sequence of events is illustrated below:
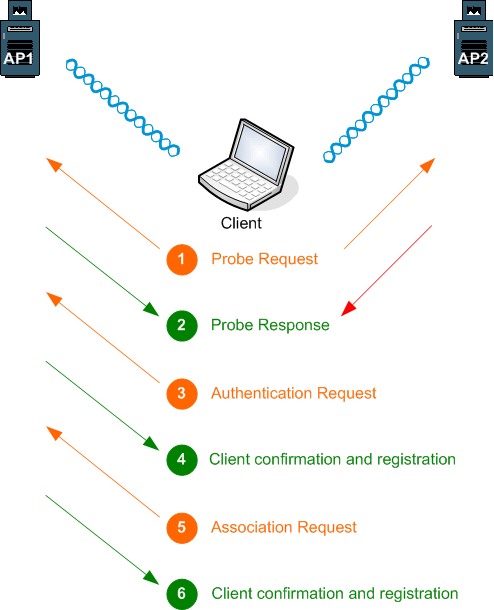
From the Probe Response the client chooses the Access Point with the best signal (in the Cisco environment, account is also
taken of the load on the AP). Because it is only the data payload that is encrypted with the key,
an incorrect key just means that decryption cannot take place. The client still associates with the AP, however
the data will not be readable.
Shared Key Authentication
The AP sends a challenge text packet to the client. The client must respond with the text
encrypted with the correct WEP key. Some systems require a MAC address to be used with the response so that
a client's MAC address must match one that has been previously entered into the APs association table.
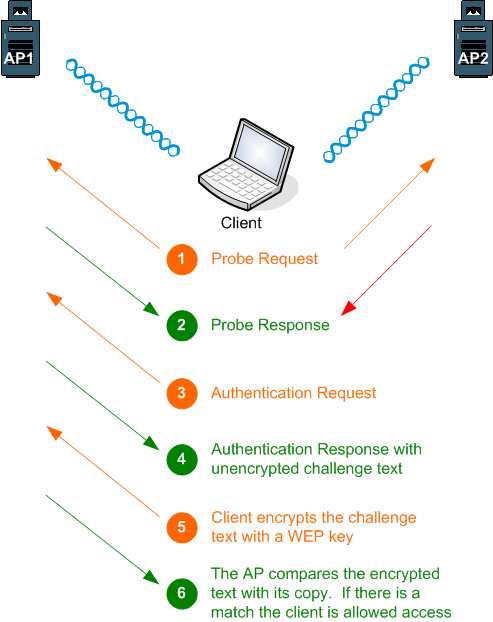
Security Loopholes with WEP
Man-in-the-Middle
The main problem with Shared Key Authentication is the unencrypted challenge text. A Man-in-the-Middle
attack could observe both the unencrypted text AND the encrypted text and thus learn the
cypher.
One example of such an attack is a Fluhrer, Mantin and Shamir (FMS)
Weak IV Attack where because the IV is changed in every packet using the Key scheduling Algorithm (KSA)
and because RC4 can sometimes generate easy to crack IV (i.e. weak) from the RC4 stream cypher, then a static WEP key
is able to be cracked within a million packets using statistical analysis.
This can be done merely by capturing the Wi-Fi traffic
and analysing it offline with a tool such as Aircrack or
Airsnort.
Such an attack is known as a Passive Attack. A Dictionary Attack could also be performed on
a passive capture by using a pre-computed dictionary of likely words and responses and working through each
possibility until a match is found.
An Active Attack may be carried out where a stream of known packets such as pings or a replay of a known traffic stream
is injected into the network towards a Wi-Fi device where a capture is taken again. Such attacks may be
IV Replay Attacks, Dictionary Attacks (with active log on attempts) or Bit Flip Attacks. See below for the attack
topology.

This topology could be used to perform a Bit Flip Attack.
The integrity of a Wi-Fi message uses Integrity Check Value (ICV) which is based upon CRC32 a 32-bit
cyclic redundancy check that can be compromised by bit-flipping. The hacker intercepts a WEP-encrypted
packet, changes the packet and then retransmits it. The packet is accepted by the Wi-Fi network at layer 2
but it is rejected by the LAN device which sends back a reply that can be predicted. The key can be derived
from a combination of a number of these replies and the changed packets.
One-way Authentication
Another issue is that authentication is one-way only i.e. the AP authenticates the client, the client
has no way of knowing if it is has associated with the correct AP.
Static WEP Keys
There is no way to dynamically generate keys
which is a major problem because with the basic WEP Open or Shared Key Authentication, WEP keys are easily cracked
and/or the MAC address is easily spoofed as the key is tied to the client device rather than the user. Because
the key is within the client machine it can reside in accessible part such as an application or the memory.
Changing WEP keys manually is unmanageable in a large network, plus there is no accounting features or integration
with existing authentication databases such as LDAP or RADIUS.
Wi-Fi Protected Access (WPA)
The problem with WEP is that the key is static and it is shared. Not only can the key become known by
a number of users, it can also be cracked relatively easily now using a 'Man-in-the-Middle' and a software
tool such as AirSnort. Enhancements were introduced to deal with these issues. First off was Cisco
with the following improvements:
- Cisco Temporal Key Integrity Protocol (CKIP) - key hashing on a per-packet basis to protect against
Initialisation Vector (IV) attacks
- Cisco Message Integrity Check (CMIC) - to protect against Replay or 'Man-in-the-Middle' attacks
- Broadcast Key Rotation so that the broadcast key changes and diminishes the chance of it being obtained
WPA was then introduced to provide some standardisation whilst the 802.11 committee instigated a more permanent
solution to the security issues. WPA was based on Draft 3 of 802.11i. The additional benefits of WPA are as follows:
- Pairwise Transient Key (PTK) - A new session key is given to the user each time the user connects to the network i.e.
on a per session basis
- Authenticated Key Management - where the user is authenticated first, followed by the generation
of a Pairwise Master key (PMK) on the client and the server. The Pairwise Master Key is used to generate the keys used to
encrypt the session. Either 802.1X or a Pre-Shared Key (PSK) may be used as the PMK
- Key management of unicast and broadcast keys
- Initialisation Vector (IV) increased from 24 to 48 bits so that the chance of a reuse of the vector (collision) is minimised
- Migration - co-existence of WEP users is allowed, although when WPA is used the WEP Shared key mechanism
is turned off, only Open Authentication is used.
- Temporal Key Integrity Protocol (TKIP) - A key hierarchy and management system where
keys are generated per packet, per session and per user, plus there is Message Integrity Check
(MIC)
Both Cisco's solution and WPA allows existing equipment to be used with only firmware or software upgrades required.
This is because the existing RC4 WEP encryption was still being utilised, the new features were designed to protect the WEP
keys, the encryption techniques used to generate the keys remained unchanged.
It may be worth making yourself familiar with 802.1X by following the link to 802.1X.
For WPA using EAP and RADIUS, the general sequence of events runs as follows for a Wi-Fi client gaining access
to a network via an Access Point:
- The client associates with an AP, however in addition to the normal 802.11 association requirements
both the client and the AP MUST agree a security capability. The SSID within the beacon probe indicates
the authentication type required, the client selects the SSID and the cypher suite that goes with the SSID.
- The client enters their credentials e.g. username and password
- Via 802.1X and an EAP method, the next sequence of steps involve the client and the RADIUS server mutually authenticating
via the AP as follows:
- The server sends a challenge to the client.
- The client carries out a hash on the password.
- The client sends this hashed password to the RADIUS in its response.
- The RADIUS server performs a hash on the password for that client in its user database.
- The RADIUS server compares the two hashed values and authenticates the client if the two values match.
- The process is then repeated in reverse so that the client can authenticate the RADIUS server that it is meant to be using.
- Once authenticated via 802.1X the server sends the client a Master Key (MK)
- Next, each of the RADIUS server and the client independently create a client-specific 256-bit Pairwise Master Key (PMK)
from the Master Key. If 802.1X is not being used, then this PMK is derived from the 64 hexadecimal Pre-Shared Key (PSK) instead.
This is moved via a RADIUS protocol attribute,
to the AP by the RADIUS server and uses the Diffie-Hellman method (see Encryption
for more information).
- Now the famous WPA 4-way handshake between the client and the AP begins:
- The AP creates a Nonce (Number used ONCE) or a random number and sends this to the client
- The client generates a nonce or random number and
a Pairwise Transient Key (PTK) is generated from the PMK. Both client and AP random numbers (nonces), plus their MAC addresses
are fed into a pseudo-random function in order to create the PTK. The PTK is used in authenticating the encryption key
and a unique PTK is unicast to each client. The client sends its own nonce, the PTK and the MIC information to the AP
- The AP sends the nonce again with its PTK that it created, and MIC key information. If this is the same PTK as that
produced by the client then this validates the client.
- The client sends MIC key information and PTK to the AP for verification, the 4-way handshake is complete because
it has been proved that the client and AP share the same PTK key information and PMK, and they are who they say they are.
In addition, the client and AP have negotiated a PTK that may be used for further key generation.
- All wireless devices associated with an access point must be able to decrypt the broadcast and multicast traffic. They do
so with the same Group Transient Key (GTK). If the AP changes the GTK because it was compromised, for example, the AP issues a
replacement key using a two-way handshake with the KEK encrypting the GTK. The Group Key 2-way handshake operates as follows:
- The AP uses a random number or the PTK to generate a Group Master Key (GMK). A group random number
is generated and this is used in conjunction with the AP MAC address to create a Group Transient Key (GTK).
The GTK is then encrypted with the EAPOL-Key Encryption Key (KEK) and broadcast (or multicast)
along with the MIC key to the clients
- The client decrypts the GTK and sends a message back to say it has done so, plus the MIC
WPA2's PTK consists of three key types. These key types are as follows:
- Key Confirmation Key (KCK) - used to check the integrity of an EAPOL-Key frame (used in the MIC)
- Key Encryption Key (KEK) - encrypts the GTK
- Temporal Keys (TK) - secure data traffic
All wireless devices associated with an access point must be able to decrypt the broadcast and multicast traffic. They do
so with the same group key, or GTK. If the AP changes the GTK because it was compromised, for example, the AP issues a
replacement key using the simpler two-way handshake with the KEK encrypting the GTK.
Because this entire process of client authentication to the RADIUS server can take up hundreds of milliseconds (if not
seconds) when a device is roaming from one AP to another, it's unacceptable for Wi-Fi phones or streaming applications on
laptops. So most enterprise wireless products have 802.11i features that help minimize roaming latency--preauthentication
and PMK caching.
Preauthentication lets a mobile client authenticate with other APs in its vicinity while remaining associated with its
primary AP. With PMK caching, a roaming client need not fully reauthenticate over 802.1X when it returns "home."
Temporal Key Integrity Protocol (TKIP)
TKIP uses existing WEP hardware that runs RC4 encryption and seeks to protect the generated keys that are vulnerable
e.g. from Weak-IV attacks.
TKIP is effectively a wrapper for WEP and operates on a per-packet basis. See below for a diagram showing the TKIP mixing
process:

Message Integrity Check (MIC)
The Michael MD5 hashing algorithm is used to perform the Message Integrity Check in order to mitigate the
Man-in-the-Middle attacks. The MIC verifies that
each packet has not been compromised and is in its original state. The following diagram illustrates how MIC works:

MIC is not a strong algorithm so a few measures have been put in place within WPA to minimise any impact
that a hacker may have. MIC has a security level strength of 20 bits which means a hacker needs 219 tries
before a forged packet has been created. An AP that sees two MIC failures within 30 seconds will
disassociate all clients within 60 seconds, and the AP does not allow any client using TKIP to associate
for 60 seconds.
802.11i
The 802.11i committee was set up to address the security issues inherent within the original 802.11
implementations. 802.11i was ratified in June 2004. Covered by 802.11i are the following:
- Central control
- The use of 802.1X (Enterprise mode) or Pre-shared Key (PSK) (Personal mode)
for Wi-Fi
- The use of Extensible Authentication Protocol (EAP)
- The use of CCMP AES instead of RC4 for encryption, TKIP is still an option. AES requires a hardware
chip change in the radio circuitry from the older RC4 chips
- More robust authentication credentials based on the user rather than the device
- Encryption keys used on a per-session basis, thereby moving away from static keys to dynamic keys
- The potential to refresh encryption keys by setting a RADIUS session timeout. This can be used
to limit a Wi-Fi user to specific time limits for access
- Mutual authentication of client and server/AP
- Access Points have to advertise security capabilities within the beacon e.g. supported unicast, multicast
and authentication types.
The Wi-Fi Alliance took these elements of 802.11i and created WPA version2. WPA2 was made to be
backwards compatible with WPA.
Rather than use RC4 (for WEP) for hardware encryption, a form of Advanced Encryption Standard (AES) is used instead.
The type of AES used is called AES Counter Mode with Cipher Block Chaining Message Authentication Code
(CBC-MAC) otherwise known as AES-CCMP (see RFC 2610).
Incidently, The US National Institute of Standards and Technology (NIST) that wanted a known royalty-free algorithm,
selected the Rijndael Algorithm to be used in AES.
Although Initialisation Vectors are used, the IV increases by one bit after each block has been encrypted
so that each cypher stream is unique. In addition, each packet is verified by using the frame length, destination
address, source address and the data to check for integrity.
With WPA2 you can use PSK with AES if no RADIUS server is available.
In Northa America WPA2 satisfies the government Federal Information Processing Standard 140-2 (FIPS 140-2)
that covers four levels of security Levels 1 to 4. This sets out requirements for all the areas
associated with the secure design and implementation of a cryptographic module.
References

|

