Network Address Translator (NAT)
Introduction
This is used when a end user's network only needs to have a few addresses available
to access the Global Internet. A table is created on the router that lists 'inside'
local addresses to 'inside' global addresses which are the legal IP addresses. This
mapping can be done statically or via the use of a dynamic pool of available legal
addresses.
Following are a number of different ways to implement NAT:
Static Address Translation
This is where one-to-one mapping is carried out between
inside local and outside global addresses.
NAT operation is illustrated in the following diagram:

Dynamic Source Address Translation
This is where individual addresses within
a pool of global addresses are dynamically mapped to local addresses.
For both static and dynamic NAT the process occurs as follows:
- An inside station connects to an outside station.
- When the first packet arrives from the inside station the router checks the NAT table.
- If no static match has been found the router carries out a translation of the inside address
to an outside address from the available pool of outside addresses by replacing the address.
The resultant mapping is saved as a 'simple entry'.
- The outside station receives the packet and replies to the outside address given
by the NAT table.
- The router carries out a lookup in its table of inside to outside address mappings and
forwards the packet to the station with the inside address.
- The packet is received and the rest of the conversation uses the NAT table.
Address Overloading
Sometimes called Port Address Translation (PAT), this is where each client uses the same IP address but uses
a different port. A good example is access to a web server. Users from a private
address, say in the 10.0.0.0 network, have their individual addresses translated to
just one legal IP address but separate port numbers between 1024 and 65535. They
can all have separate conversations with a web server having just one address and destination
port of 80 (HTTP). This applies just as well if one user has several sessions with the same
web server, the different port numbers distinguish the sessions.
The process operates as follows:
- An inside station connects to an outside station.
- When the first packet arrives from the inside station the router checks the NAT table.
- If no static match has been found the router carries out a translation of the inside address
to an outside address from the available pool of outside addresses by replacing the address.
The resultant mapping is saved as an 'extended entry'. If other inside addresses want to
connect to outside stations then the same IP address is used but a different TCP port
is utilised to distinguish the conversations.
- The outside station receives the packet and replies to the outside address given
by the NAT table.
- The router carries out a lookup in its table of inside to outside address and port mappings and
forwards the packet to the station with the inside address.
- The packet is received and the rest of the conversation uses the NAT table.
Overlapping Networks
There may be times when addresses in the inside network overlap with addresses in the outside
network, see below for an example:
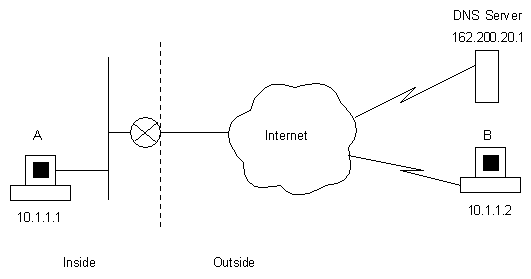
The process operates as follows:
- Host A is on the inside network and wants to talk to Host B so it sends a Name-to-address
lookup to the DNS server at 162.200.20.1.
- The router intercepts the DNS reply that contains the address.
- Because the address for Host B overlaps the address scheme used on the internal network
the router translates the address to an address from a separate pool of outside
addresses, in this case say 20.1.1.2.
- The DNS reply is then forwarded to Host A and A thinks that B has the address 20.1.1.2.
- Host A opens a connection to 20.1.1.2.
- The router receives the packet and replaces the source address of 10.1.1.1 with
an inside global address of say 30.1.1.1 and saves the mapping.
- In addition, the router replaces the destination address of 20.1.1.2 with Host B's actual
outside global address of 10.1.1.2 and saves the mapping.
- Host B receives the packet thinking that it came from 30.1.1.1 and replies accordingly.
- The conversation continues using the NAT table double lookup.
TCP Load Distribution
This is where a number of machines on the inside
deal with a certain connection from the outside world. The Global to Local Mapping
scheme is first established and then an access list is set up to determine the
address that is allowed to be accessed by the outside world. Next, a rotary group
is set up that has a number of server addresses that take the outside connections
to this particular IP address on a round robin basis. This spreads the traffic
load and is ideal for Web servers.
The process of operation is as follows:
- An outside user opens a connection to an inside virtual host, say 10.1.1.200.
- The router translates the address from the virtual address to a real host
address, say 10.1.1.1 and forwards the packet.
- Host 10.1.1.1 receives the packet and responds.
- The router performs a NAT table lookup and forwards the packet to the outside address.
- The next connection to the virtual host is translated to another inside address e.g.
10.1.1.2 and the process is repeated for that address.
This round robin approach means that a number of hosts can take the strain rather than just
one host.
Port Forwarding
Port forwarding is really an extension of static NATting of addresses by adding port mapping within the IP header.
Commonly client devices are 'hidden' behind routers or firewalls that NAT the client private addresses to public addresses.
Normally these inside client devices initiate communication with the Internet and NATting happens dynamically on the router.
Although these client devices are inside devices they can sometimes provide services to devices ouside of
the firewall, that is, these client devices can act as servers that require to be accessed from outside.
If an outside device wishes to access a TCP or UDP port on an inside device e.g. a protected web server, then the port that
the outside device is attempting to access e.g. port 80, needs to be forwarded in the traffic destined for the inside
device. The IP header needs to be modified in order to achieve this. Take the following example where an outside device with
IP address 222.22.22.1 using port 1234 i.e. 222.22.22.1:1234, is accessing a web server address given as the router
WAN interface 233.33.33.1:80. The web server actually sits on the inside of the router and the router NATs the internal IP
address of the server to the WAN interface. The HTTP port 80 however, is forwarded to the inside web server.
The packet headers will look like the following sequence:
| Location |
Source IP |
Source Port |
Destination IP |
Destination Port |
| From outside device to WAN interface |
222.22.22.1 |
1234 |
233.33.33.1 |
80 |
| From WAN interface to inside web server |
222.22.22.1 |
1234 |
192.168.1.10 |
80 |
| From inside web server to WAN interface |
192.168.1.10 |
80 |
222.22.22.1 |
1234 |
| From WAN interface to outside device |
233.33.33.1 |
80 |
222.22.22.1 |
1234 |
Outside devices that initiate communication to these inside 'servers' are a security risk so it is important to
configure the port forwarding carefully so that you do not let more traffic in than necessary. If you have a number of
inside devices that are acting as servers then you can set up the port forwarding specifically for each service.
Typical application ports that require port forwarding to a server on the inside are as follows:
| Application |
Incoming Port |
| HTTP |
80 |
| SSL |
443 |
| FTP |
21 |
| Telnet |
23 |
| IMAP |
143 |
| SIMAP (IMAP over SSL) |
933 |
| SSL/POP2 (POP3 over SSL) |
995 |
| SMTP |
25 |
| SSH |
22 |
| Finger |
79 |
| NNTP |
119 |
| GOPHER |
70 |
| NTP |
123 |
| PPTP |
1723 |
| Carbon Copy 32 |
1023-1680 |
| Citrix |
1494 |
| Laplink |
1547 |
| Lotus Notes |
1352 |
| Netmeeting |
1720, 1503 |
| PC Anywhere |
22, 5631-5632 |
Typical game ports that require port forwarding to a server on the inside are as follows:
| Game |
Incoming Port |
| Alien vs Predator |
80, 2300-2400, 8000-8999 |
| Dark Reign 2 |
3100, 3568, 3999 |
| Dune 2000 |
1140-1234, 4000 |
| Elite Force |
26000, 27500, 27910, 27960 |
| Everquest |
1024-6000, 7000 |
| F-22 Lightning 3 |
4533-4660 |
| Half Life |
27015 |
| Hexen II |
26900 (add '1' for each player) |
| Heritic II |
28910 |
| MSN Gaming Zone |
6667, 28800-29000 |
| MSN Gaming Zone - DX |
2300-2400, 47624 |
| Myth |
3453 |
| Need for Speed |
9442 |
| Need for Speed 3 |
1030 |
| Quake II |
27910 |
| Quake III |
27960 (add '1' for each player) |
| Tiberian Sun |
1140-1234, 4000 |
Having any ports open to the Internet is risky bearing in mind the continuous port probing that
goes on. Some of the games and applications require a great many ports to be open and this can create
an insecure environment.
Configuration of Port Forwarding may seem complex. It does not help that different routers and firewalls use different
terminology for the same thing. A commercial level router will have comprehensive facilities for defining rules
of access. These are often called IP filters or Access Lists. The domestic routers operate a web menu approach
to configuration and may already have a predefined list of applications or firewall rules that you are able to select
from. The more sophisticated domestic routers will allow you to add services where you can customise
the IP address ranges and ports for which you are allowing access. Some routers may even use the term
Port Forwarding within the menu structure.

Copyright � 1996 - 2025, Rhys Haden.
|

